Blog
-
how to check size of zimbra mail accounts from terminal
The most easy way to see the size of all zimbra mailboxes is to ssh into your zimbra server and type the following:
$ su - zimbra $ all_accounts=
zmprov -l gaa; for account in $all_accounts; do mbox_size=zmmailbox -z -m $account gms; echo "Mailbox size of $account = $mbox_size"; done ; -
bluedio T7 language reset
Bluedio T7 is nice until it defaults to a language you don’t get. Manual does not say much about switching languages. Search engines didn’t helped either. What we did is try several combinations and we were lucky by simultaneously pressing [+] [-] [play] and the so called “multi function” button. Press everything at the same time a couple of times and you’ll end up in english or any other supported language you want.
By the way, Bluedio T7 is good for listening music and audio in general, noise canceling does a nice job, battery duration is at acceptable levels, even 1 year after first purchase. It’s also equipped with a mic but it’s far from perfect: the other party thinks like sound comes from a loudspeaker. T7 sensor auto stops music when you wear off headphones – when you get used to it proves to be a great feature.
-
install php sqlsrv driver on ubuntu 20.04
Suppose you want to access a data source that lies on microsoft sql server dbms — most probably installed on a windows server machine, although mssql server is now a well fit also on linux machines (see: Ubuntu: Install SQL Server on Linux – SQL Server | Microsoft Docs, btw, this guide is tested a couple of times on ubuntu 20.04, and is actually consisted of 3-4 simple commands you should run and you get a sql server running on a nice cheap linux machine).
Let’s focus on installing the mssql php driver. First of all you should install build essentials, otherwise you won’t be able to build programs with gcc. You should also install odbc development. These are two important prerequisites not necessarily preinstalled on typical bare vps hetzner vps. So, first step is:
sudo apt-get install build-essential
sudo apt-get install unixodbc-devThen, install odbc:
Install the Microsoft ODBC driver for SQL Server (Linux) – SQL Server | Microsoft Docs
After that, follow the guide on:
Linux and macOS Installation for the Drivers for PHP – SQL Server | Microsoft Docs
This guide is also test on others versions of php (7.4) not necessarily php8.
I hope this is useful.
-
repost: php w/c api, simple http request using guzzle
composer require guzzlehttp/guzzle woocommerce api
<?phprequire_once"vendor/autoload.php";useGuzzleHttp\Client;define('WC_CONSUMER_KEY', 'PASTE_CONSUMER_KEY_HERE');define('WC_CONSUMER_SECRET', 'PASTE_CONSUMER_SECRET_HERE');$client= newClient(['base_uri'=> 'YOUR_DOMAIN_BASE_URL',]);try{$response= $client->request('GET', '/wp-json/wc/v3/products/PRODUCT_ID_HERE', ['headers'=> ["Authorization"=> "Basic ". base64_encode(WC_CONSUMER_KEY.':'.WC_CONSUMER_SECRET)],'verify'=> false, //only needed if you are facing SSL certificate issue]);$body= $response->getBody();$arr_body= json_decode($body);$response= $client->request('GET', '/wp-json/wc/v3/products', ['headers'=> ["Authorization"=> "Basic ". base64_encode(WC_CONSUMER_KEY.':'.WC_CONSUMER_SECRET)],'query'=> ['include'=> $arr_body->related_ids, ],'verify'=> false,]);$body= $response->getBody();$arr_products= json_decode($body);if(!empty($arr_products)) {foreach($arr_productsas$product) {?><p><a href="<?php echo $product->permalink; ?>"><?php echo$product->name; ?></a></p><?php}}} catch(Exception $e) {echo$e->getMessage();}If you use Laravel and prefer not to reinvent the wheel, this lib is pretty good too: GitHub – Codexshaper/laravel-woocommerce: WooCommerce Rest API for Laravel
-
reveal wifi password on windows 10
If your user profile has administrative privileges, open command prompt and type:
netsh wlan show profile name="nice hotspot" key=clear
-
how to solve freepbx upgrade failed: Class ‘Whoops\Util\TemplateHelper’ not found
Although freepbx upgade processes are typically well designed and tested, there might be specific configurations in some installations that could lead into failures. One of these failures occured into one of our freepbx 12 installations while we were upgrading it into version 13 of freepbx. We’ve initiated the upgrade process from the freepbx web gui and clicked-skipped the typical upgrade steps where step 3 reported the fatal error:
Submitting data to servers...Done Running checks...Passed <strong>Stage 1</strong> Bumping FreePBX to version 13...Done Checking online servers...Done Downloading 13 Framework......Done Installing 13 Framework...ERROR: Try running this manually on the CLI to finish: 'amportal && fwconsole ma upgradeall'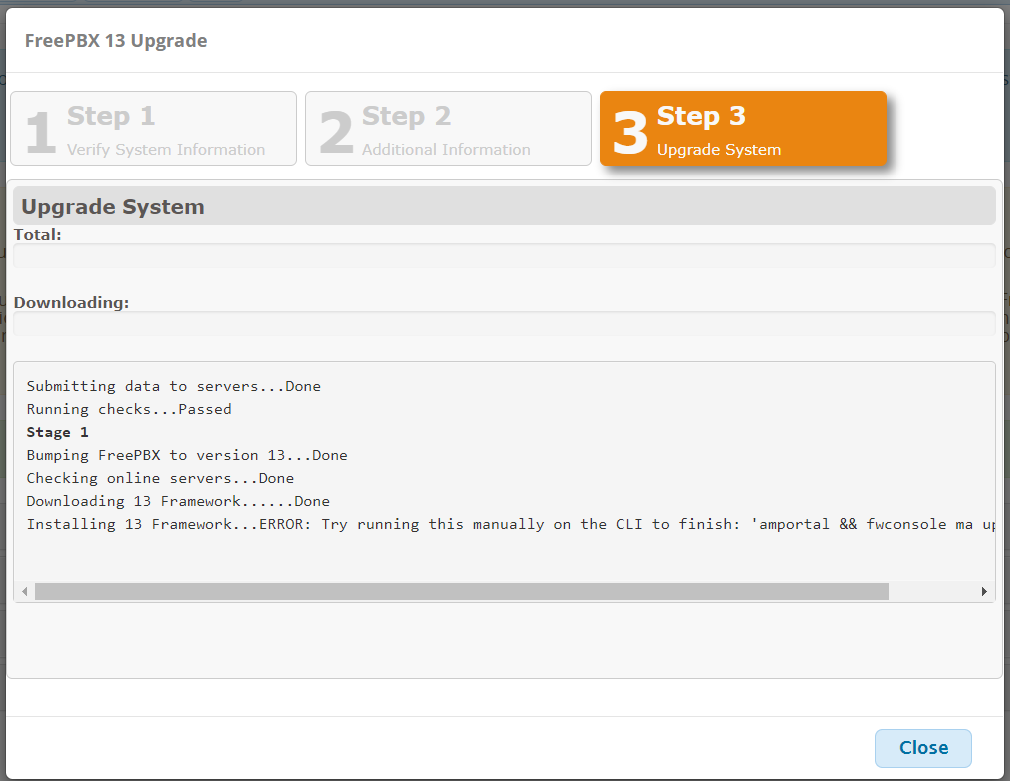
We note that before-installation-checks haven’t reported any warnings.
We’ve directly logged in via ssh and ran the suggested:
amportal && fwconsole ma upgradeall
which also failed.
Thanks to Class ‘Whoops\Util\TemplateHelper’ not found – General Help – FreePBX Community Forums we’ve followed the spartan suggestion of tm1000 Andrew Nagy to run
fwconsole --fix_zendAnd it worked!
The explanation was that there was an old zend module breaking the upgrade process and –fix_zend solved the problem.
Hope this works for you too.
-
composer update: mmap() failed: [12] Cannot allocate memory PHP Fatal error: Out of memory
proc_open(): fork failed errors#
If composer shows proc_open() fork failed on some commands:
PHP Fatal error: Uncaught exception 'ErrorException' with message 'proc_open(): fork failed - Cannot allocate memory' in pharThis could be happening because the VPS runs out of memory and has no Swap space enabled.
free -m total used free shared buffers cached Mem: 2048 357 1690 0 0 237 -/+ buffers/cache: 119 1928 Swap: 0 0 0To enable the swap you can use for example:
/bin/dd if=/dev/zero of=/var/swap.1 bs=1M count=1024 /sbin/mkswap /var/swap.1 /sbin/swapon /var/swap.1You can make a permanent swap file following this tutorial.
Please check also this article: https://getcomposer.org/doc/articles/troubleshooting.md
-
npm to add sb-admin-2 to laravel
First of all make sure you have node.js installed. If you haven’t so, install it:
Change directory to your laravel project and use npm to install sb-admin-2 like this:
npm install --global startbootstrap-sb-admin-2
If it compains for popper or other packages, use npm again to install them, like this:
npm install --global popper
Now, the tricky part for most people new to this:
Go to laravel path
resources/sass/app.scss
Add this import:
@import "~startbootstrap-sb-admin-2/scss/sb-admin-2.scss";
Don’t forget to:
npm install npm run dev
Now change your app.blade.php with html markup from sb-admin-2, save and refresh your browser: you will end up with sb-admin-2 powerful laravel installation.
-
existing code to bitbucket (git)
Let’s assume you ‘ve got setup a small project locally and it’s time to add it to bitbucket.
All you need to know is: https://confluence.atlassian.com/bitbucketserver/importing-code-from-an-existing-project-776640909.html
There are a couple of details though that could make your life difficult if you don’t pay the proper attention:
- Bitbucket. Login to your bitbucket account, create a repo (but pay attention!) without adding any READMEs, nor GITIGNOREs. Repo must be empty, otherwise *push* will fail. Now, use clone button top-right corner && copy https version of the URL.
- Locally. Open your prompt to your project directory.
git init git add --all git commit -m "Initial Commit" git remote add origin {{copied_url}} git push -u origin masterDone!