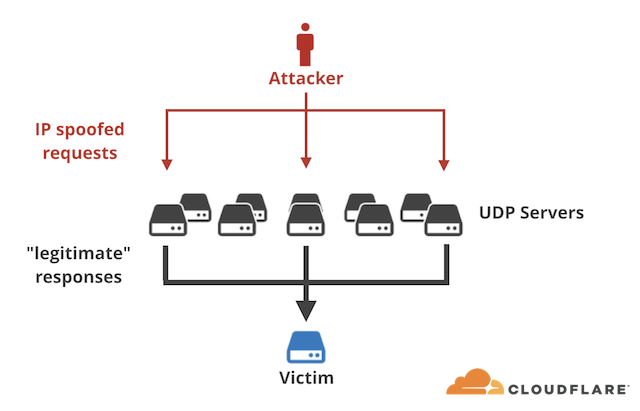
Zimbra uses memcached and if not properly configured could lead to a vulnerable system.
If you want to read more on memcached attack read this:
https://blog.cloudflare.com/memcrashed-major-amplification-attacks-from-port-11211/
How to resolve this vulnerability in 3 steps:
- Enable firewall on your server
- Setup zimbra specific rules
- Bind memcached to localhost
- Deny memcached port from localhost
Let’s start.
Enable firewall on your server
To resolve memcached vulnerability on zimbra systems you have to enable firewall, if it’s not already enabled. On ubuntu, you could use ufw. To check whether ufw is already enabled:
sudo ufw status verboseYou can find a nice guide here:
https://www.digitalocean.com/community/tutorials/how-to-set-up-a-firewall-with-ufw-on-ubuntu-14-04
To sum up main steps of the article above:
- Make sure ufw is installed
- Check whether it’s running or not
- Important! Make sure you preserve yourself from locking out of your system. Enable ssh port whether it is 22, 2222 or whatever is it.
- Enable firewall.
sudo ufw enableSetup zimbra firewall rules
This is not difficult but you have to be careful to not forget some important zimbra port. I include some basic port below.
sudo nano /etc/ufw/applications.d/zimbra
If file does not already exist create it.
Add the following contents.
[Zimbra] title=Zimbra Collaboration Server description=Open source server for email, contacts, calendar, and more. ports=22,25,80,110,143,161,389,443,465,514,587,993,995,7071,11211/tcp
Save the file and enable newly configured rules.
Important! Before enabling, make sure you have ssh port open (ufw allow ssh).
sudo ufw allow Zimbra sudo ufw enable
To check the status of ufw:
sudo ufw status verbose
For more details, consult the following article:
Bind memcached to localhost
For Zimbra Single Server Installation
Configure memcached to listen on 127.0.0.1 only to avoid this attack. Use below commands.
su - zimbra /opt/zimbra/bin/zmprov ms `zmhostname` zimbraMemcachedBindAddress 127.0.0.1 /opt/zimbra/bin/zmprov ms `zmhostname` zimbraMemcachedClientServerList 127.0.0.1
Restart service:
zmmemcachedctl restart
Reference:
https://wiki.zimbra.com/index.php?title=Blocking_Memcached_Attack
Deny memcached port from localhost
UFW rules for Ubuntu servers
Drop all connections to port 11211.
ufw deny 11211
Accept connections from localhost.
ufw allow from 127.0.0.1 to any port 11211
Accept connections from other proxy servers. Run below two commands for each proxy server IP in your zimbra setup.
ufw allow from <Proxy1 IP> to any port 11211
Reference:
https://wiki.zimbra.com/index.php?title=Blocking_Memcached_Attack
More interesting articles on Zimbra:
Leave a Reply